When we talk about Mobile Business then its worst useful without authentication means to make Network as business all user required to be authenticate lets understand how authentication done in gsm.
Authentication center (auc in gsm, authentication center in gsm)
Authentication Center (AUC)
The AUC is a processor system, it performs the “authentication” function. It will normally be co-located with the Home Location Register (HLR) as it will be required to continuously access and update, as necessary, the system subscriber records.
The AUC/HLR centre can be co-located with the MSC or located remote from the MSC. The authentication process will usually take place each time the subscriber “initializes” on the system.
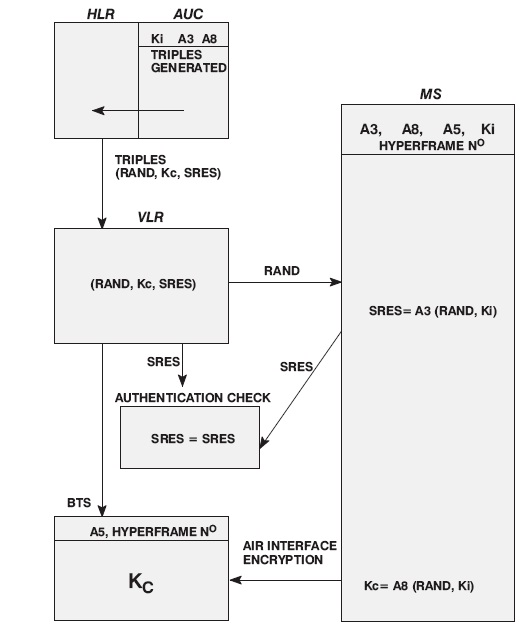
Authentication Process
To discuss the authentication process we will assume that the VLR has all the information required to perform that authentication process (Kc, SRES and RAND). If this information is unavailable, then the VLR would request it from the HLR/AUC.
1. Triples (Kc, SRES and RAND) are stored at the VLR.
2. The VLR sends RAND via the MSC and BSS, to the MS (unencrypted).
3. The MS, using the A3 and A8 algorithms and the parameter Ki stored on the MS SIM card, together with the received RAND from the VLR, calculates the values of SRES and Kc.
4. The MS sends SRES unencrypted to the VLR
5. Within the VLR the value of SRES is compared with the SRES received from the mobile. If the two values match, then the authentication is successful.
6. If cyphering is to be used, Kc from the assigned triple is passed to the BTS.
7. The mobile calculates Kc from the RAND and A8 and Ki on the SIM.
8. Using Kc, A5 and the GSM hyperframe number, encryption between the MS and the BSS can now occur over the air interface.
Note: The triples are generated at the AUC by:
- RAND = Randomly generated number.
- SRES = Derived from A3 (RAND, Ki).
- Kc = Derived from A8 (RAND, Ki).
- A3 = From 1 of 16 possible algorithms defined on allocation of IMSI and creation of SIM card.
- A8 = From 1 of 16 possible algorithms defined on allocation of IMSI and creation of SIM card.
- Ki = Authentication key, assigned at random together with the versions of A3 and A8.
The first time a subscriber attempts to make a call, the full authentication process takes place.
However, for subsequent calls attempted within a given system control time period, or within a single system provider’s network, authentication may not be necessary, as the data generated during the first authentication will still be available.
How Authentication Center (AUC) Works in GSM?
In GSM (Global System for Mobile Communications), the Authentication Center (AUC) is a critical component responsible for securing user identity and ensuring the confidentiality and integrity of communication. It plays a vital role in the authentication process, verifying that the user attempting to connect to the network is legitimate. The AUC is part of the GSM core network and works in conjunction with the Home Location Register (HLR) and other network elements.
Authentication Process in GSM
The authentication process in GSM involves several steps, all of which are aimed at preventing unauthorized access to the network and ensuring the security of user data. The AUC performs the key task of generating and managing the authentication parameters used in this process.
- Step 1 – Authentication Request: When a mobile device (UE – User Equipment) attempts to connect to the network, it sends an authentication request to the base station (BTS). This request is forwarded to the MSC (Mobile Switching Center) and then to the AUC.
- Step 2 – Challenge Generation: The AUC generates a random challenge (also known as RAND) along with a signed response. This challenge is unique and is generated using a secret key (K) that is stored in the AUC and shared with the Subscriber Identity Module (SIM) in the mobile device.
- Step 3 – Sending Challenge to Mobile: The AUC sends the RAND and the signed response to the MSC, which forwards it to the mobile device.
- Step 4 – Response from Mobile Device: The mobile device receives the challenge, processes it using the stored secret key (K) from the SIM, and generates a response called the SRES (Signed Response). The mobile device sends the SRES back to the MSC.
- Step 5 – Verification: The MSC forwards the SRES back to the AUC, which compares the received response with the one it generated earlier. If the responses match, the authentication is successful. If they do not match, access is denied.
Key Functions of the Authentication Center (AUC)
- Key Management: The AUC manages the encryption keys and authentication parameters used in the network. It ensures that the keys used for authentication remain secure and are only accessible by authorized entities.
- Generation of Authentication Tokens: The AUC is responsible for generating the RAND and SRES tokens that are used in the authentication process. These tokens ensure that each authentication session is unique and secure.
- Data Integrity and Confidentiality: The AUC helps ensure the integrity of the signaling messages by using cryptographic algorithms, thus protecting the data exchanged between the mobile device and the network from unauthorized access or tampering.
- Subscriber Identity Protection: The AUC plays a key role in protecting the subscriber’s identity by ensuring that sensitive information, such as the IMSI (International Mobile Subscriber Identity), is never transmitted over the air without encryption.
Role of AUC in Network Security
The Authentication Center is crucial in maintaining the overall security of the GSM network. Without it, unauthorized users could easily access network resources, potentially leading to fraud and security breaches. The AUC ensures that only legitimate users can access the network by validating their credentials during the authentication process.
In addition to authentication, the AUC also plays a role in key management, providing the necessary cryptographic keys to establish secure communication channels between the mobile device and the network. These keys are used to encrypt voice and data transmissions, ensuring that the user’s communication remains private and secure.